Defend against Malware Virus that keeps creating index.php and .htaccess
We all know why bad actors infect sites: monetary gain, boosts in SEO ratings for his or her malware or spam campaigns and a number of other reasons explained in our post on hacker’s motivations.
It defeats the aim of the attack if the malware is easily and quickly removed for WordPress website. Attackers have developed some methods for shielding their work as we will explore in this post.
Cyber Attacks Stats
Cyber-attacks are happening more than you even think, we are sharing some stats which will blow your mind:
- Daily attacks: 12,340,754 (Full day have not passed yet, About 3H and 30 minutes left)
(Twelve million three hundred forty thousand seven hundred fifty-four)
- Weekly cyber-attacks (7d): 86,385,278
(Eighty-six million three hundred eighty-five thousand two hundred seventy-eight)
- Monthly cyber-attacks (30d): 370,222,620
(Three hundred seventy million two hundred twenty-two thousand six hundred twenty)
- Yearly (365d): 4,504,375,210
(Four billion five hundred four million three hundred seventy-five thousand two hundred ten)
If we round about the full attacks, then it will be over 5-billion cyber-attacks every year!
Note: All figures are counted using one day data!
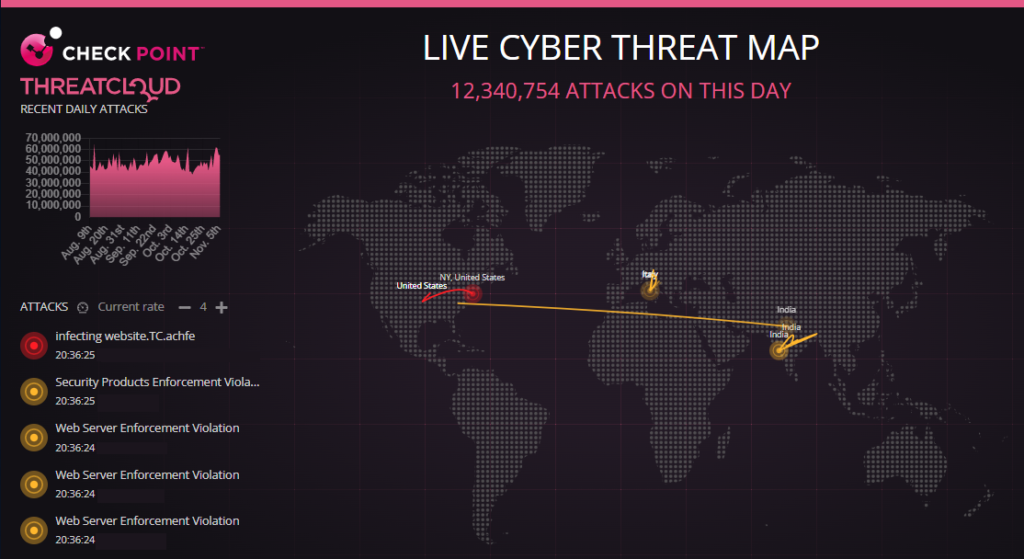
Credits: Live Cyber Threat Map
What does this malware look like?
Your infected htaccess looks like image mentioned below, with some file names mentioned index, content, lock360, admin, wp-login, wp-theme, wp-scripts and wp-editor.php (the files available in wordpress)
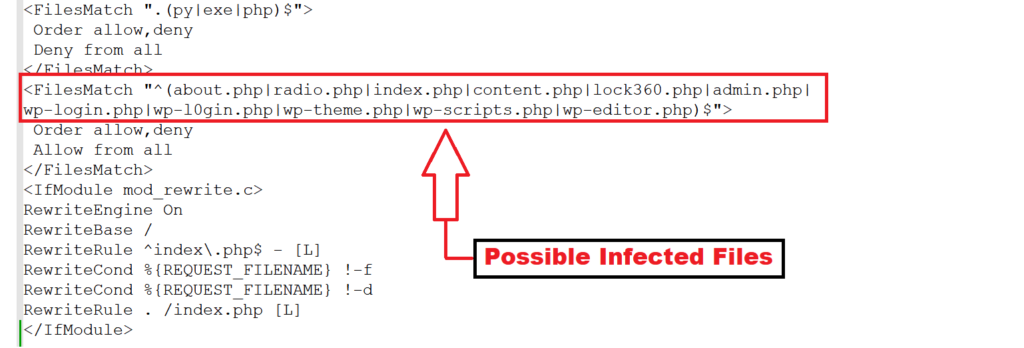
<Start of code>
<FilesMatch ".(py|exe|php)$">
Order allow,deny
Deny from all
</FilesMatch>
<FilesMatch "^(about.php|radio.php|index.php|content.php|lock360.php|admin.php|
wp-login.php|wp-l0gin.php|wp-theme.php|wp-scripts.php|wp-editor.php)$">
Order allow,deny
Allow from all
</FilesMatch>
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteBase /
RewriteRule ^index\.php$ - [L]
RewriteCond %{REQUEST_FILENAME} !-f
RewriteCond %{REQUEST_FILENAME} !-d
RewriteRule . /index.php [L]
</IfModule>
</End of code>
Example of an infected index.php file that automatically re-generates itself through a malicious process running within the background.

It doesn’t matter if your site isn’t running WordPress, the attackers will usually replace the index.php with an infected copy of the WordPress index.php file.
Sometimes hundreds or thousands of infected htaccess files scattered throughout the website directories.
This is often designed to prevent modified PHP files or tools from running on the site or to allow the malicious files from running in case there’s some mitigation already in place.
Example of another infected file which interferes with the power to run most PHP scripts by generating report calls to their server, one example is attached below:
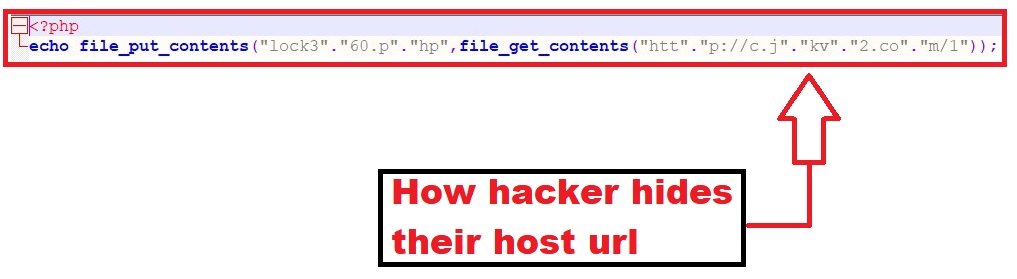
In rare circumstances, the attackers will leave a replica of the original index.php file on the server named old-index.php or 1index.php that we will rename back to index.php.
In most cases, the infected files will be changed to permissions and attempting to remove or clean those files directly is unsuccessful since the malware will immediately create a new infected copy.
Cleaning the infection
In this blog we will discuss what is the best protection against malware. As you have already seen from the infected htaccess example above, the attackers have created an inventory of files allowed to run on the server.
Search for the below-mentioned files and either remove them or scan them for viruses depending on your situation:
- about.php
- radio.php
- index.php
- content.php
- lock360.php
- admin.php
- wp-login.php
- wp-l0gin.php
- wp-theme.php
- wp-scripts.php
- wp-editor.php
Preventing the other PHP files from loading. These files will normally does not exist on the server but possibly can run as malicious processes. The persistent, running processes on the server are what allows the malware to automatically and immediately reinfect the location once the infection is removed.
The first attempt to stop the virus is to create a file from one of those names and add the following:
For instance: In “radio.php”
Note:
The file name must match one among those listed in htaccess as those are the only files that are allowed to run on the server. this may ensure our command is successfully run.
The contents of this file will search for all running PHP processes and attempt to stop those. we will then load that file in the browser.
You won’t see any content within the browser but if the process was successful, you ought to be able to rename or delete htaccess and index.php without seeing a new infected copy being created. If you’re not able to access the file you created, you’ll need to proceed with the SSH steps below.
It is important to note that some malware may not re-create the infected files immediately, and you’ll want to load your site a couple of times, checking for the reinfected files after each attempt.
Once you’ve got confirmed that the files are not going to return, you’ll need to remove the remainder of the infection.

Proceeding via ssh (Advance)
If previous attempts to clean the infected index.php or htaccess have been unsuccessful, then you are required to gain SSH access or load terminal on your CPanel to check running processes.
Run the top command (and press the ‘c’ key to expand the output) or “PS -aux” and look for anything strange there. Mostly these cases will show something like this:
wp-content/uploads/2023/lock360.phpOr like this:
wp-includes/1.phpA malicious process running on the server designed to immediately re-infect the website once files are modified.
This can be seen by running “PS -aux” or “top”
In above case, we can see the process running with similar PID and we can kill that process.
The “kill” command attempts to terminate the specified process and the -9 flag will attempt to “force quit” it.
If the offending process was responsible for recreating index.php, you should be able to rename the file without seeing a new copy dropping in, and you should be able to proceed with cleaning the remainder of the infection.
Conclusion
Though attackers are always trying to find new ways to infect sites,
There are some common steps you’ll take to minimize those infections:
- Put your website behind a Firewall.
- Regularly update things related to your site like passwords etc.
- Keep all plugins, themes and your CMS up so far at all times; remove any unneeded plugins or themes – attackers are always on top of new and undiscovered vulnerabilities.
- Stop cross site contamination (means don’t host multiple websites developed in different technologies on same server)
As Web development company, we also provide Website Security Services, please check them out as well.
Frequently Asked Questions (FAQ’s):
1. What Is Cybersecurity?
A: Cybersecurity is a broad term but to put it simply. It means securing the data
2. What types of businesses are most at risk for a cyberattack?
A: Big businesses or those who have sensitive data usually have the technology and regulations to protect themselves from cyberattacks.
While small to medium business do not felt spending on these data and usually often face cyber-attacks.
3. What’s one of the biggest cybersecurity challenges businesses facing?
A: One of the biggest challenges is to stay aware of evolving cyberthreats!
4. Are organizations doing enough to combat cyberthreats?
A: No, it usually required education, lots of infrastructure, manpower and huge spendings.
So only typical groups are doing enough research and failed to prevent cyber-attacks!
5. What are the most prominent cyberthreats?
A: Ransomware is biggest issue right now, this case can be triggered by fake ads, cracked software,
Free resources like pictures (Read more about here), phishing and not having enough knowledge on How to protect yourself while you are online.
Have some time? Visit our website or Pinterest page to know more.

